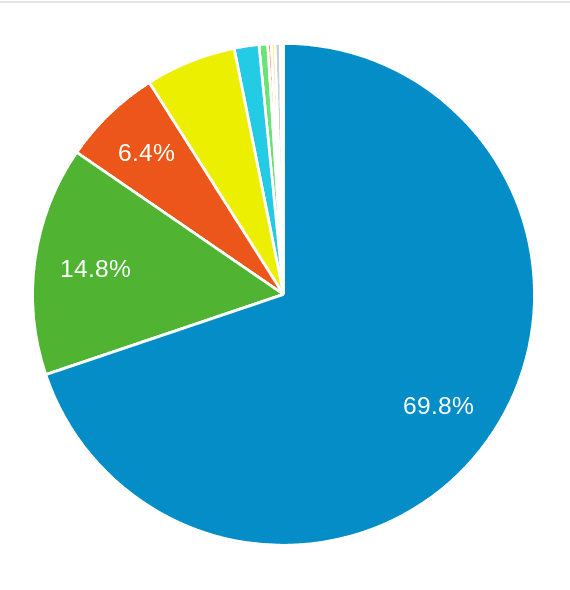
This is a guest post by Alyssa Tong, who runs the Jenkins Area Meetup program and is also responsible for Marketing & Community Programs at CloudBees, Inc. |

Happy 2018! The Jenkins World train is ready to take off once again. As usual, the sign of festivities looming begins with the Call for Papers. Those who attended Jenkins World 2017 know that Jenkins World 2018 is coming back to San Francisco. But what they did not know is that Jenkins World will also be coming to Europe. You read that right, Jenkins World is taking place in two locations in 2018:
Jenkins World USA | San Francisco | September 16 - 19, 2018
Jenkins World Europe | October - date and location TBA
To encourage open collaboration and stimulate discussions that will help advance Jenkins adoption and drive it forward, we invite Jenkins users, developers and industry experts to submit a speaking proposal to Jenkins World San Francisco and or Europe. Submissions for both locations are being accepted now and will close on March 18, 2018 @ 11:59PM Pacific.
Where do I go to submit my proposal?
Submissions for both Jenkins World USA and Europe are accepted at:
Can I make proposal(s) to both conferences?
Yes, you can! Once you’ve created an account on the CFP website you will be given the option to make submission(s) to one conference or both conferences.
Important Dates:
CFP Opens: January 17, 2018
CFP Closes: March 18, 2018 @ 11:59pm Pacific
CFP Notifications: April
Agenda Announcement: April
Event Dates:
Jenkins World USA | San Francisco | September 16 - 19, 2018
Jenkins World Europe | October - exact date TBA